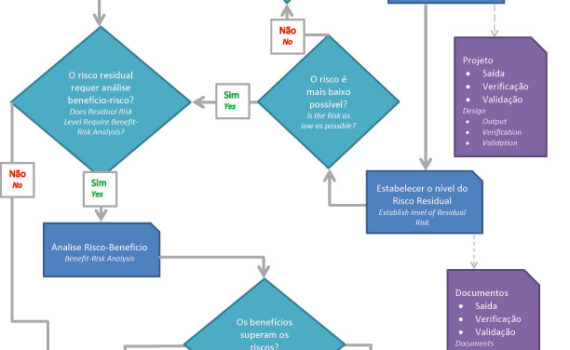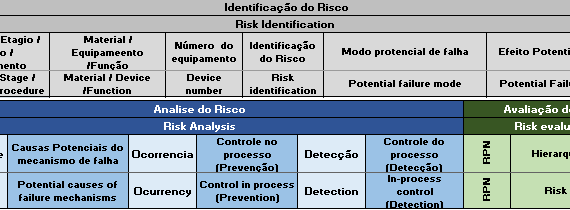
The FMEA analysis aims to identify potential failure modes of a product or process in order to assess the risk associated with these failure modes so that they are classified in terms of importance and then receive corrective actions in order to reduce the incidence of failures . […]